Kubernetes Networking : Fundamentals of Kubernetes Networking
Welcome to this new series of article for Kubernetes networking, my goal is to give you all the information needed to not feel lost and to understand everything you should need when it comes to the Networking of Kubernetes.
We’ll explore the basics of Kubernetes networking, including the networking model, core components, and common networking solutions. This will give you a solid foundation for understanding the more advanced topics we'll cover in later articles.
I will do a 5 part series :
- #1 Fundamentals of Kubernetes Networking
- #2 Pod-to-Pod and Service Networking
- #3 Network Security and Ingress Controllers [In Progress]
- #4 Service Meshes and Advanced Networking [In Progress]
- #5 Best Practices and Future Trends [In Progress]
1- Understanding The Kubernetes Networking Model
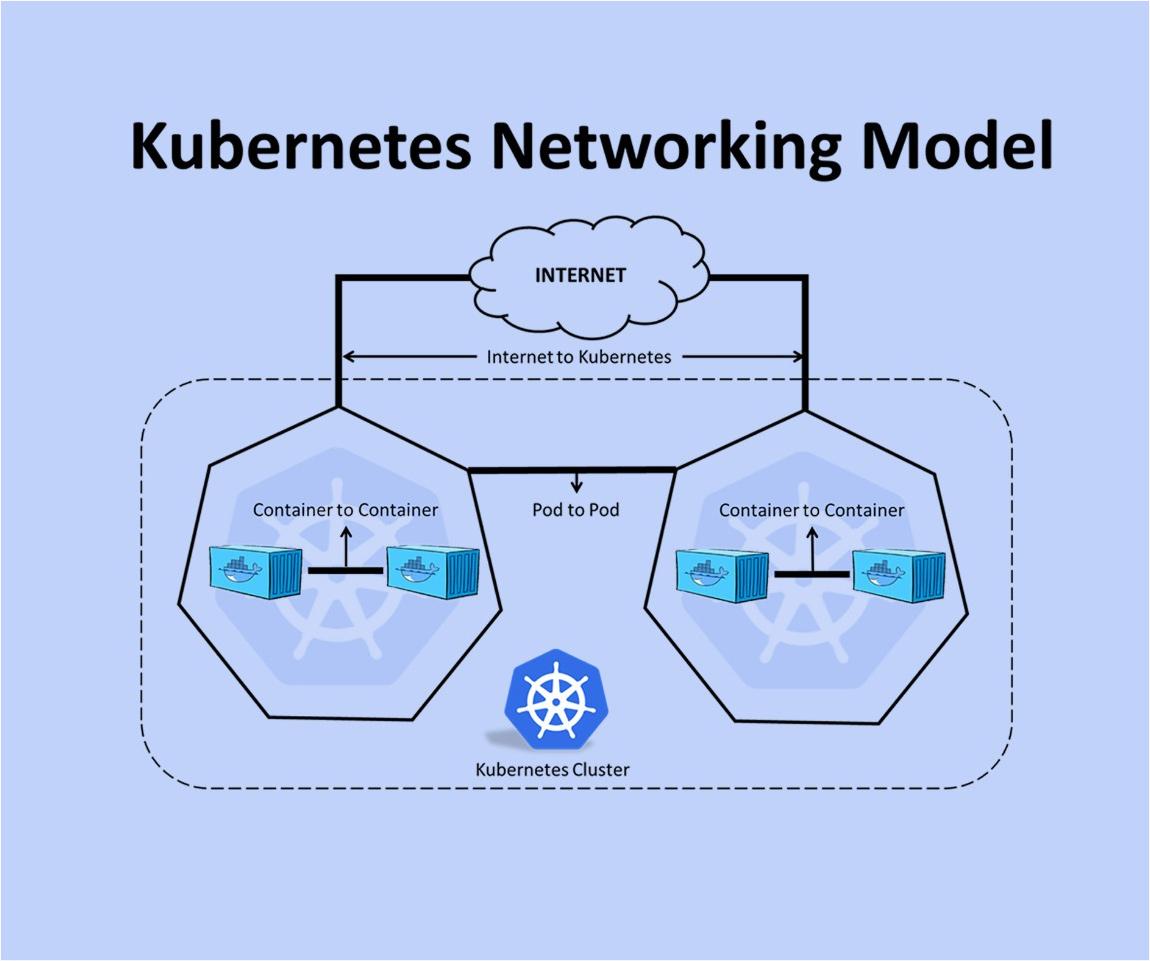
Networking in Kubernetes revolves around a unique and robust model that ensures efficient communication between various components. Understanding the key aspects of this model is crucial to deploying and operating Kubernetes effectively.
1.1 Overview of Kubernetes Networking
Kubernetes networking is essential for application communication within a cluster. The networking model is designed to solve several challenges that arise when deploying and managing containerized applications:
- Flat Netowrking:
- Kubernetes employs a flat networking model, where all Pods can communicate with each other without Network Address Translation (NAT).
- It simplifies communication, as every Pod has its own IP address and can directly communicate with other Pods.
- A flat network means that all Nodes and Pods are on a single network, without any subnets or segmentation.
- Cluster Networking:
- The cluster network is shared by all Pods and Nodes in the Kubernetes cluster.
- It allows seamless communication across all components, both intra and inter-Node.
- Service Abstractions:
- Kubernetes uses Services to provide stable network endpoints for a set of Pods.
- These Services act as load balancers and provide consistent IP addresses and DNS names, facilitating communication between different parts of an application or between applications.
- Network Plugins:
- Kubernetes relies on network plugins known as CNI (Container Network Interface) plugins to implement networking.
- These plugins manage the network configuration for Pods and provide different networking capabilities.
1.2 Core Networking Requirements
To maintain seamless communication, Kubernetes imposes several key requirements on the network infrastructure:
1.** Pod-to-Pod Communication:**
- All Pods in a Kubernetes cluster should be able to communicate directly with each other, without the need for NAT.
- This ensures that distributed applications can function correctly, as they often require communication between various Pods.
- Node-to-Pod Communication:
- The IP address that a Pod sees itself as should be the same IP address that other Pods and Nodes see it as.
- This consistency is curcial for applications relying on knowing their own IP, as well as for network policies and service discovery.
1.3 Networking in Pods, Nodes and the Cluster
Kubernetes networking encompasses several layers of communication, including:
- Networking in Pods:
- Pods are the smallest deployable units in Kubernetes and represent single instances of an application.
- Each Pod has its own IP address, which is unique within the cluster.
- Containers within a Pod share the same network namespace, which means they can communicate with each other using localhost.
- Networking in Nodes:
- Nodes are the machines that run the Pods in a Kubernetes cluster.
- Each Node has a range of IP addresses that it can allocate to the Pods running on it.
- Nodes communicate with each other over the cluster network, enabling inter-Node communication.
- Networking in the Cluster:
- The cluster network is a flat network shared by all Pods and Nodes.
- This network allows seamless communication across the entire cluster, regardless of where the Pods and Nodes are located.
- The cluster network is typically implemented using overlay networks, which encapsulate network traffic to provide seamless connectivity.An overlay network is a virtual network that is built on top of another network.
We've explored the Kubernetes networking model, including an overview of how it works, the core requirements, and how networking functions at different layers within the cluster. Understanding these concepts is essential for anyone looking to deploy and manage applications on Kubernetes.
2- Basic Networking Components
In this section, we'll talk in more details about the fundamental networking components of Kubernetes. We’ll cover Pods, Services, Network Policies, and DNS in Kubernetes, all of which play a key role in Kubernetes networking.
2.1 Pods
Pods are the smallest deployable units in Kubernetes, typically representing one or more containers that share the same context. Let’s go into the details:
Pods are designed to encapsulate application containers, storage resources, a unique network identity (IP address), and other configurations:
- Containers:
- A Pod can have one or more containers running within it.
- The containers share the same network namespace, which means they can communicate with each other using localhost.
- Multiple containers in a Pod are often used for closely related functions, such as a main application container and a sidecar container that helps with logging or monitoring.
- Networking:
- Each Pod has a unique IP address within the cluster.
- Pods can communicate with each other directly using these IP addresses.
- The IP address of a Pod is typically assigned from the range of IPs available on the Node where the Pod is running.
- Lifespan:
- Pods are ephemeral, meaning they can be created, destroyed, and replaced.
- When a Pod is replaced, the new Pod will have a different IP address, which is important to consider when designing applications.
How do Pods communicate with each other?
- Direct Communication:
- Pods can communicate directly with each other using their IP addresses.
- This direct communication is straightforward when Pods are on the same Node, as they share the same local network.
- For Pods on different Nodes, communication occurs over the cluster network.
- Pod-to-Service Communication:
- Direct communication between Pods can become cumbersome as Pod IPs are ephemeral.
- Instead, Kubernetes provides Services to enable stable communication, which we’ll explore next.
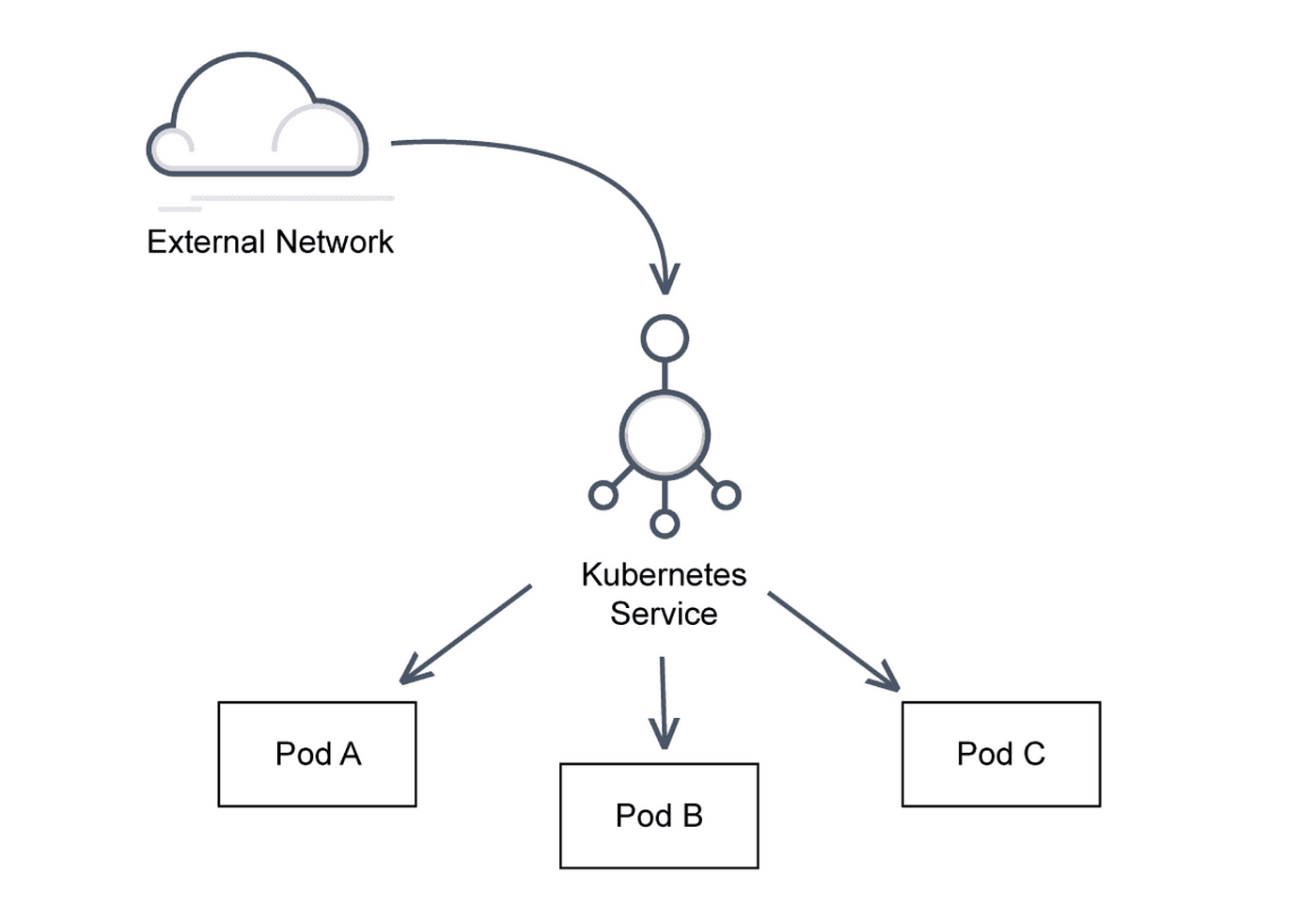
2.2 Services
Services are an abstraction that defines a logical set of Pods and a policy by which to access them. They are a crucial part of Kubernetes networking because they provide stable endpoints for applications and manage load balancing:
- Types of Services
- ClusterIP:
- The default type of Service.
- Exposes the Service on a cluster-internal IP, which means the Service is only accessible from within the cluster.
- Ideal for internal communication between different parts of an application.
- NodePort:
- Exposes the Service on a specific port on each Node, which allows external traffic to reach the Service.
- The Node’s IP address and the allocated port are used to access the Service.
- LoadBalancer:
- Exposes the Service externally using a cloud provider’s load balancer for example.
- Provides a stable IP address and balances traffic across the Pods.
- ExternalName:
- Maps a Service to the contents of the externalName field (e.g., a DNS name).
- Used for integrating external services or exposing internal services with custom DNS names.
- Service Proxies:
- Services use kube-proxy to handle routing and load balancing.
- kube-proxy runs on each Node and maintains network rules for directing traffic to the appropriate Pod.
- Service Discovery
- Services can be discovered using their names or through DNS.
- Kubernetes provides built-in DNS to resolve Service names to IP addresses.
2.3 Network Policies
Network Policies are a Kubernetes resource that controls the traffic allowed to and from Pods:
- Purpose:
- Network Policies provide a way to enforce security controls between Pods and other network entities.
- They are useful for restricting communication to only what is necessary, which enhances security.
- Use Cases:
- Isolation because by default, all Pods can communicate with each other. Network Policies can isolate Pods or groups of Pods.
- Security because Network Policies can prevent unintended communication, which helps to secure sensitive workloads.
- Implementation:
- Network Policies are implemented by the CNI plugin used in the cluster.
- Different plugins may offer varying levels of support and features for Network Policies.
2.4 DNS in Kubernetes
DNS is a fundamental part of Kubernetes networking, enabling name resolution for Pods and Services:
- Built-in DNS:
- Kubernetes has a built-in DNS Service that provides name resolution for Services and Pods.
- This Service is typically backed by CoreDNS, which is a flexible and extensible DNS server.
- Service and Pod DNS:
- Each Service gets a DNS entry in the format
service-name.namespace.svc.cluster.local - This allows Pods to refer to Services by name, even if the underlying IP addresses change.
- Pods can also have DNS entries, which can be customized through annotations or other configurations.
- DNS Resoltion:
- DNS resolution allows applications to refer to each other by name, which is easier to manage and more robust than using IP addresses directly.
- The built-in DNS Service ensures that name resolution is consistent across the cluster.
We've covered in this section the basic networking components in Kubernetes, including Pods, Services, Network Policies, and DNS. Each of these components plays a crucial role in Kubernetes networking, enabling communication within the cluster and with external networks.
3-Kubernetes Networking Tools
Kubernetes networking relies on various tools and plugins to handle the complexities of network communication within and across clusters. In this section, we'll cover some of the most common networking solutions available in Kubernetes and how to choose the right Container Network Interface (CNI) for your cluster.
3.1 Common Networking Solutions

Kubernetes networking is modular, allowing different solutions to be plugged in based on your needs. These solutions implement the CNI specification, providing networking functionality for Pods and Services. Here, we will explore some of the most common and widely used solutions:
- Flannel:
- Overview:
- Flannel is a simple and easy-to-configure networking solution.
- It creates an overlay network using VXLAN or other mechanisms, which enables Pod-to-Pod communication across Nodes.
- Flannel operates on Layer 3 of the OSI model, providing IP connectivity.
- Use Cases:
- Ideal for small to medium-sized clusters.
- Useful for those who want a straightforward setup without advanced features.
- Calico:
- Overview:
- Calico provides networking and network policy capabilities.
- It operates at Layer 3, using BGP (Border Gateway Protocol) to distribute routing information between Nodes.
- Calico also supports eBPF (extended Berkeley Packet Filter) for efficient packet processing.
- Use Cases:
- Suitable for environments requiring advanced networking and security features.
- Useful for enforcing complex network policies and ensuring high-performance networking.
- Weave Net:
- Overview:
- Weave Net creates a mesh overlay network for Kubernetes clusters.
- It provides encrypted communication and uses fast data paths for efficient packet delivery.
- Use Cases:
- Ideal for secure networking needs.
- Suitable for environments where simple and robust networking is desired.
- Cilium:
- Overview:
- Cilium provides advanced networking and security using eBPF.
- It operates at Layer 3 and 4, offering features like network policies, load balancing, and deep packet inspection.
- Use Cases:
- Ideal for environments requiring high security and deep observability.
- Suitable for advanced networking needs where performance is critical.
- Other Solutions:
- Kube-router:
- A network plugin that provides Pod networking, network policy, and service proxy functionality.
- Useful for those who want a unified solution integrating various aspects of networking.
- Open vSwitch (OVS):
- A multilayer virtual switch used for advanced networking setups.
- Suitable for environments requiring complex networking configurations.
Each of these solutions has its strengths and weaknesses, catering to different needs and use cases.
3.2 Choosing the Right CNI for Your Cluster
Choosing the right CNI for your Kubernetes cluster depends on several factors, including the size of your cluster, your networking requirements, and the features you need. Here’s how you can decide which CNI is right for you:
- Cluster Size:
- For small to medium-sized clusters, simpler solutions like Flannel or Weave Net are often sufficient.
- For larger clusters or environments requiring advanced routing, solutions like Calico or Cilium are more suitable.
- Networking Features:
- If you need basic networking without advanced features, solutions like Flannel or Weave Net are ideal.
- For environments requiring network policies, load balancing, or deep packet inspection, solutions like Calico or Cilium are better suited.
- Security:
- If security is a primary concern, consider solutions that offer robust network policies and encryption, such as Calico or Weave Net.
- Cilium, with its eBPF-based packet processing, also provides high-security capabilities.
- ** Performance:**
- For high-performance networking, solutions like Calico with eBPF or Cilium are excellent choices.
- These solutions provide efficient packet processing and low-latency communication.
- Comlexity:
- If you want a straightforward setup without much configuration, Flannel or Weave Net are good options.
- For more complex and feature-rich environments, Calico, Cilium, or OVS are suitable.
- Integration:
- Consider the integration with other tools and services you may be using.
- For example, if you need advanced service proxy functionality, kube-router might be a good choice as it integrates networking and service proxies.
In this section, we've explored the common networking solutions available for Kubernetes and how to choose the right CNI for your cluster. Each solution caters to specific use cases, ranging from simple networking to advanced security and performance.
The choice of CNI depends on factors like cluster size, networking features, security, performance, complexity, and integration.
4- Conclusion
The Kubernetes Networking series goal is to equip you with a comprehensive understanding of how networking functions within Kubernetes. This first article provided a foundational understanding of the Kubernetes networking model, core components, and essential networking tools.
Key Takeways:
- Kubernetes Networking Model:
- We saw the unique networking model used by Kubernetes, which revolves around the concepts of flat networking, seamless communication between Pods, and the use of network plugins.
- This model ensures that all Pods and Nodes within a cluster can communicate with each other directly, without Network Address Translation (NAT).
- Core Networking Components:
- We covered the key networking components, including Pods, Services, Network Policies, and DNS.
- Pods are the smallest deployable units, each with a unique IP address, while Services provide stable network endpoints.
- Network Policies offer fine-grained control over communication, and DNS facilitates name resolution for Pods and Services.
- Networking Tools:
- Kubernetes networking relies on various tools and plugins to manage network communication.
- We explored common solutions like Flannel, Calico, Weave Net, and Cilium, each offering different features and catering to different use cases.